In March, PeckShield’s data revealed a significant milestone in the recovery of stolen cryptocurrency funds, with approximately $100 million successfully reclaimed from hacking incidents. Despite initial losses amounting to millions of dollars, an impressive 52.8% of the pilfered funds found their way back to their rightful owners.
The majority of these recovered funds stemmed from the Munchables incident, where negotiations prompted the hacker to return the ill-gotten cryptocurrency haul.
PeckShield’s Report: Crypto Hacks Dip in March, But Still Surpass January Figures
According to a report released on April 1 by web3 cybersecurity firm PeckShield, the crypto market endured over 30 hacking incidents in March, resulting in losses totaling $187.29 million, of which $98.8 million was recovered. Although this marks a 48% decrease from February, when hackers plundered over $360 million, March’s losses still surpassed those of January, which amounted to $182.5 million.
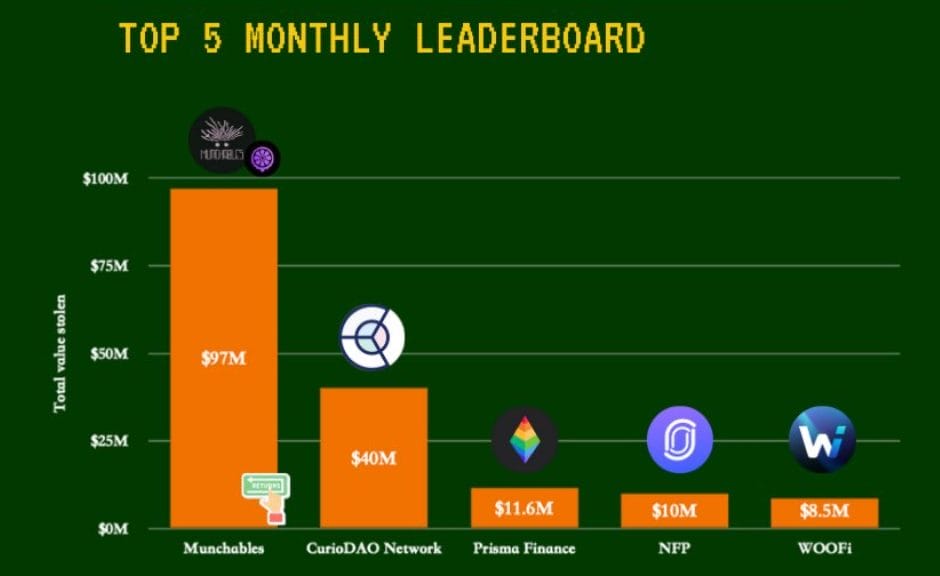
The report also spotlighted the top five incidents during the month. Leading the pack was the Munchables hack, followed by breaches at Curio, Prisma Finance, NFPrompt, and the WOOFi exploit.
Source: PeckShield
The recovered funds predominantly originated from the Munchables incident, a non-fungible token (NFT) game on the Blast network. After disclosing an exploit on March 26, resulting in estimated losses of $62 million, the project was surprised when the hacker voluntarily returned the funds without any ransom demands.
Subsequently, on March 27, Munchables identified the hacker as one of its developers, and Blast core contributors announced the recovery of $97 million in stolen crypto funds.
Similarly, in the Prisma Finance incident, which saw around $11 million in stolen digital assets, negotiations between the protocol and the hacker are underway after the latter claimed the exploit was a “white hat rescue.”
On March 24, Curio’s MakerDAO-based smart contract on Ethereum suffered a breach, initially estimated at $16 million in losses. However, PeckShield suggests the actual figure may be closer to $40 million, making it the second-largest loss incident last month.
The fifth-largest incident involved NFPrompt, backed by Binance, experiencing unauthorized access, leading to roughly $10 million in losses, while the WooFi decentralized exchange recorded losses of approximately $8.5 million.
Q1 2024: Decline in Crypto Hacks and Fraudulent Activities, Total Losses Reach $336.3 Million
During the first quarter of 2024, losses from hacking and fraudulent activities totaled approximately $336.3 million, down from $437.5 million in 2023. The report outlines 46 hacking incidents and 15 cases of fraudulent activities during this period.
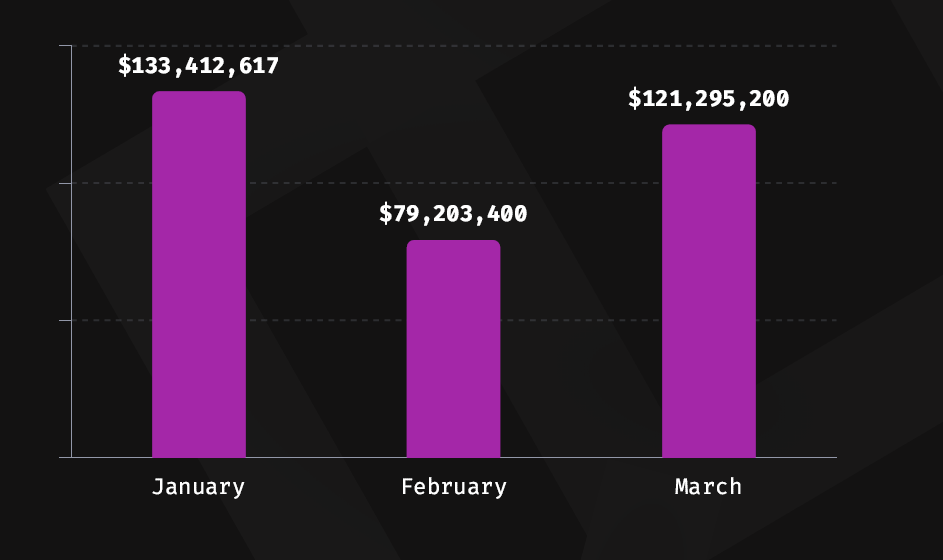
Two projects accounted for significant losses, totaling $144.5 million, comprising 43% of the overall loss. The largest attack, amounting to $81.7 million, targeted the cross-chain bridge protocol Orbit Bridge on New Year’s Eve.
January witnessed the highest monthly losses in Q1, totaling $133 million. The second-largest attack of the quarter involved a $62 million exploit on Munchables. Overall, $73.9 million (22%) of the stolen funds from seven exploits in Q1 were successfully retrieved. The number of attacks decreased by 17.6%, from 74 in Q1 2023 to 61 in 2024.
Hacking incidents dominated the losses, accounting for 95.6% ($321.6 million) across 46 incidents, while fraudulent activities, scams, and rug pulls made up 4.4% ($14.7 million) in 15 incidents.
Ethereum emerged as the most targeted blockchain, followed by the BNB Chain, with both networks accounting for 73% of the total losses. Ethereum experienced the highest number of attacks, with 33 incidents constituting 51% of the total losses.
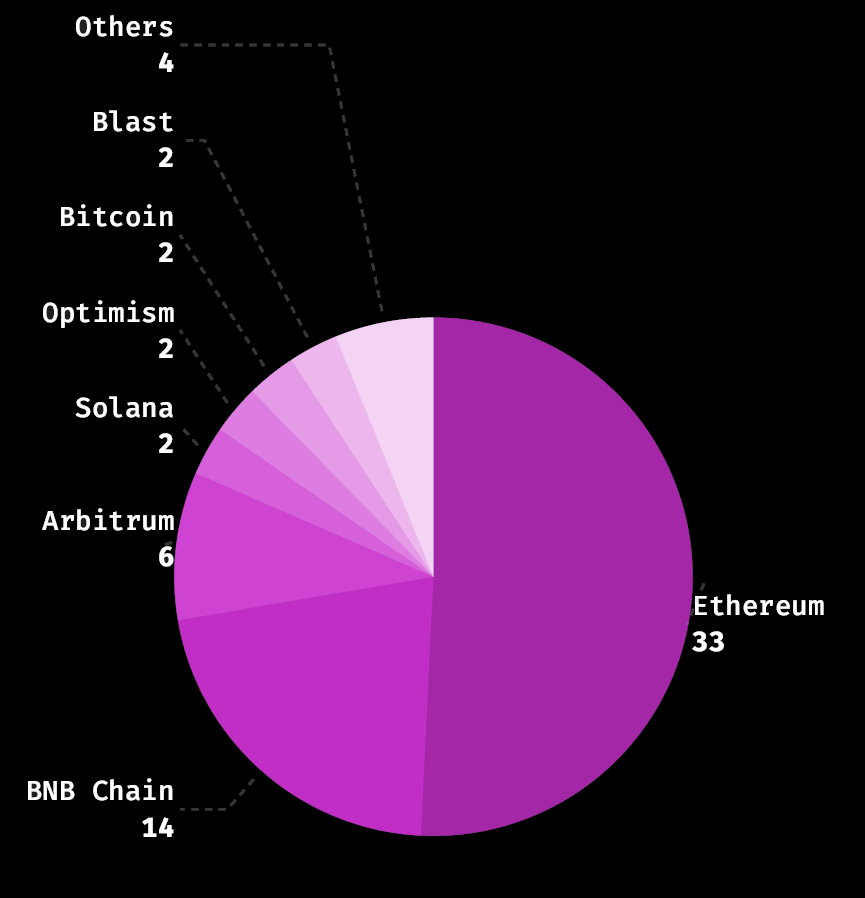
Meanwhile, the BNB Chain encountered 12 attacks, representing 22% of the exploited funds. Additional incidents occurred on Arbitrum, Solana, Optimism, Bitcoin, Blast, Polygon, Conflux Network, and Base.
